1. Introduction
The Security Audit Log is a tool designed for auditors who need to take a detailed look at what occurs in the SAP system. By activating the audit log, you keep record of those activities you consider relevant for auditing. This information is recorded on a daily basis in an audit file on each application server. You can then access this information for evaluation in the form of an audit analysis report. Statistical information can easily be retrieved on transactions and reports. Although it was not designed for this purpose, the information it generates is invaluable when estimating the number of resources needed for the next upgrade project and when you want to know to which transactions or reports most attention and effort should go to.
The following information can be recorded in the Security Audit Log:
- Successful and unsuccessful dialog and RFC logon attempts
- RFC calls to function modules
- Successful and unsuccessful transaction and report starts
2. Activating the audit log
The following instance profiles must be set in order to activate audit logging (use transaction RZ10 to do so).
rsau/enable: Set to 1 to activates audit logging
rsau/local/file: Name and location of the audit log file
rsau/max_diskspace/local: Max. space of the audit file. If maximum size is reached auditing stops.
rsau/selection_slots: Max. number of filters
The settings are activated after the instance has been restarted.
3. Defining Filters
To access the Security Audit Log configuration screen from the SAP standard menu, choose:
Tools-> Administration->Monitor->Security Audit Log->Configuration (or transaction SM19).
Filters define what needs to be recorded. The following information can be specified:
- Which User(s), Client(s) (wildcards can be used)
- Audit class (for example, dialog or RFC attempt, start of transaction, report...)
- Importance of the event (critical, important...)
Filters can be static (permanently) or dynamic (temporarily):
- Static filters are stored inside the database. All application servers use the same filter for determining which events should be recorded in the audit log. After saving (Save) and activating (Profile->Activate) the static profile, it will be loaded at the next restart of the application server.
- Dynamically created profiles, on the contrary, can be activated at any time to filter for selected events. They are automatically distributed to all active application servers (after saving and distributing them by selecting Configuration->Distribute Configuration).
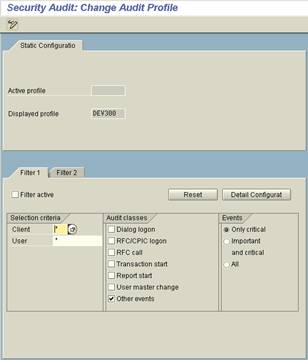
Transaction SM19 - Administer Audit Profile4. Analyzing the Audit Log
The Security Audit Log produces an audit analysis report that contains the audited activities. By using the audit analysis report you can analyze events that have occurred and have been recorded on a local server, a remote server, or all of the servers in the SAP System.To access the Security Audit Log Analysis screen from the SAP standard menu, choose:
Tools->Administration->Monitor->Security Audit Log->Analysis (or transaction SM20). The Audit Log can be scanned for a period of time, user, transaction, report, ect.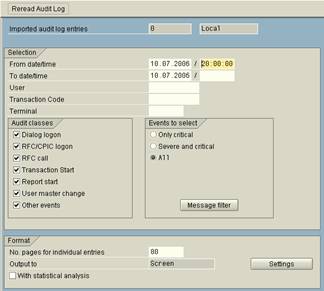
Transaction SM20 - Analyzing the Audit LogExample report:
Time Cat No Cl. User Transaction code Terminal MNo Text
12:00:38 DIA 0 100 I004567 SM19 PCIT0012 AU3 Transaction SM19 Started
12:00:56 DIA 1 100 I003765 SE71 PCIT0054 AU3 Transaction SE71 Started
12:01:28 DIA 1 100 I003765 SE71 PCIT0054 AUW Report RSTXDBUG Started
12:01:31 DIA 1 100 I003765 VT03N PCIT0054 AU3 Transaction VT03N Started
12:01:36 DIA 1 100 I003765 SE71 PCIT0054 AU3 Transaction SE71 Started
12:01:43 DIA 1 100 I003765 SE71 PCIT0054 AUW Report RSTXDBUG Started
12:01:45 DIA 1 100 I003765 VT03N PCIT0054 AU3 Transaction VT03N Started
12:01:58 DIA 1 100 I003765 VT12 PCIT0054 AU3 Transaction VT12 Started
12:01:58 DIA 1 100 I003765 VT10 PCIT0054 AUW Report RV56TRST Started
12:01:58 DIA 1 100 I003765 VT10 PCIT0054 AUW Report RV56TRSL Started
12:02:49 DIA 1 100 I003765 VT03N PCIT0054 AU3 Transaction VT03N Started
T r a n s a c t i o n S t a t i s t i c s
Transaction Number of entries
VA01 17 5%
VA02 13 4%
SE71 13 4%
SE16N 12 3%
ZV01 9 1%
SM19 9 1%
SE38 8 1%
SA38 7 1%
MB51 7 1%
CO03 5 1%
VT03N 5 1%
SE37 4 1%
SE91 4 1%
LX03 4 1%
VA01 3 1%
SE09 3 1%
SM18 3 1%
CO02 2 1%
BMBC 2 1%
R e p o r t S t a t i s t i c s
Report Number of entries
RSBTCRTE 653 24 %
ZFIN01 642 23 %
SAPMSSY4 298 11 %
ZCO03 297 11 %
ZFIN09 74 3 %
SAPLSMTR_NAVIGATION 40 1 %
RSRZLLG0 39 1 %
RSDSLAN1 33 1 %
CSM_LOAD_APPSRV_DATA 33 1 %
SAPMSSY8 31 1 %
RSDSBUFF 31 1 %
RSDSOSCO 31 1 %
RSDSFSYS 31 1 %
RSDSUSER 31 1 %
RSDS_DBMEMBER 31 1 %
RSDSDEFLOAD 31 1 %
RSALSUP5 30 1 %
RSRZLST0 30 1 %
RSALSUP2 30 1 %
RSUVM018 30 1 %
RSDSSPTI 30 1 %
CCUMEAS 30 1 %
RSRFCDMN 30 1 %
RSDSSPNR 25 1 %
RSDS_BP_FREEWP 16 1 %
RS_UPDATE_STATUS 14 1 %
RK_SE16N 6 %5. Reorganizing the Audit Log
The Security Audit Log saves its audits to a corresponding audit file on a daily basis. Depending on the size of your SAP System and the filters specified, you may be faced with an enormous quantity of data within a short period of time.Old audit log files can be deleted via Tools->Administration->Monitor ->Security Audit Log->Configuration (or transaction SM18).


2 comments:
This post is probably where I got the most useful information for my research. Thanks for posting, maybe we can see more on this.
Are you aware of any other websites on this
sap-security Online training
nice post.
Sap ABAP On Hana training
SAP Grc training
SAP Secrity training
oracle sql plsql training
Post a Comment