How to Earn Rs.25000 every month in internet without Investment?
SAP Security Guide Volume 1 & 2 Material free downloads
Security And Control Update Handbook
SAP Security Guide Volume 1 & 2
SAP Security Guide Vol - 3
Audit Information Approach
Security In SAP Systems
SAP Security Administration
Security Design For Coca-Cola
Security Management
Security Foundation
SCOT Configuration Material free download
SCOT Configuration
One document for easy SAP.doc
kernel_download_swdc.rar
Checklist For Basis Consultant.rar
How to Configure SAP Library.ppt
Call Management .rar
SAP R/3 Overview
History Of SAP
SAP Products Reference
Using SAP in Education and Reference
SAP Upgrade Guide Material free downloads
Upgrading the kernel 620 to 640.rar
Component Upgrade Guide Windows
Component Upgrade To 4.7
SAP Upgrade 4.6 SR2
SAP Systems Upgrade from 3.x - 4.6
SAP Upgrade 4.6c On Unix
SAP Upgrade Guide
SAP Upgrade Guide To 4.6b
SAP Upgrade Master Guide To ECC 5.0
SAP Upgrade to 4.6b on NT
SAP Upgrade To 4.5b
System Switch Upgrade
Transition And Upgrade to MYSAP ERP
Upgrade Of MYSAP
ECC Customer based Upgrade
SAP R3 Customer based Upgrade
Customer based Upgrade
ERP 6.0 Upgrade
SAP Performance Tuning material free download
Scheduled Daily Tasks
Scheduled Weekly Tasks
Scheduled Monthly Tasks
Scheduled Quarterly Tasks
Scheduled Annual Tasks
Analyzing SAP Buffers
Performance in a Nutshell
Performance Optimization using Data Archiving
Planning and Conducting high volume load tests
Performance Tuning for SAP BW
SAP Performance Optimization Guide
SAP Press BW Performance Optimization Guide
SAP Performance Tuning
Database Security For Oracle material free downloads
Database Security For Oracle
Check For OracleEntries
MCOD Introduction
Database SetupAnd Tuning
Oracle 9i backup and Recovery Concepts
Oracle 9i Security and network Integration Guide
Oracle 9i Database Administration Guide
BIT660 Data Archiving
Step by Step Process Of Data Archiving
Oracle DBA
Oracle Database Administration With SAPDBA
Upgrade to Oracle 9.20 On Windows
BR Tools Screen Shots free download
BR Tools Screen Shots
BR Tools Overview
BR Tools All Tablespace Info
BR Tools Resizing A Data File
BR Tools Starting And Stopping The Database
BR Tools Toogle Archive Mode Log
BR Tools Instance Status
BR Tools Adding Data File To The Table Space
Backup Strategy For Oracle
BR Backup
BR Connect_620
Use of BR Tools
BR Tools To Backup Oracle
BR Tools With Oracle Recovery Manager
EMC Legato_SAPAG
Robot_Oracle_BR Tools
SAP Backup tools
Backup And Recovery Guide
BR Connect
BR Space
BR*tools support for Heterogenous System Copy
T-code sa38
SA38 is used to run programs or reports in SAP. This Tcode is highly critical. This tcode is generally not given to any one int Production and quality environment. Only Virsa firefighter ids and SUPER users has this tcode.
enter SA38 in the command field on top left corner and hit enter key.
Then you will see the screenThen enter the program name and press F8 key or click on execute button

Then you will see the program screen......
After that i hope you know what you are supposed to do.
When you add SA38 to a role menu the following objects gets added
S_PROGRAM
and authorization groups.
the S_PROGRAM object contains the following values
SUBMIT
BTCSUBMIT
VARIANT
SUBMIT allows one to run a program.
BTCSUBMIT allows the user to Schedule a background job for the execution of a program.
VARIANT allows user to maintain variants for the program.
These three can be given depending upon the policy of the customer.
There is another tcode SE38 which has same functionality as SA38 but can do a lot more than sa38
T-code SU24
SU24 gives you the list of authorization objects that are checked when an tocde is executed. For example when you enter tcode mbo2 there are many authorization objects checked for the transaction to be executed successfully. This tcode gives all of the authorization objexts that are checked or included for checking during the execution of this tcode. A security consultant will have acces to su24 transaction. This is helpful when dealing with su53 dumps.
Goto transaction Su24 you will end up with a screen as shown below
Then enter transaction like ME28 ( int the figure different Tcode is used)
and press F8 key. Then you will see the following screen. Here you can see list of objects that has will be checked during execution of the tcode. The objects with proposal values (last column) set to YS will be checked and are added to the profile when the tcode is entered in role menu.
Here you can see list of objects that has will be checked during execution of the tcode. The objects with proposal values (last column) set to YS will be checked and are added to the profile when the tcode is entered in role menu.
Click on the image to see full view.
And the color indicator (first column) green === globally active
light gray OR DIAMOND shape == globally inactive objects which are not checked in any case.
The objects with proposal YS are checked definitely. The objects with proposal NO will not be checked normally. They will be checked based on the input entered in the tcode.
as you can see the last but one column is global check indicator which indicates whether the object is disabled globally or not.
What is and authorization object
An authorization object is a collection of fields. Each field can have many values.
For example S_TABU_DIS has two fields.
Authorization Field | Long Text |
DICBERCLS | Authorization group |
ACTVT | Activity |
This authorization object is checked when tcode se16 (table display) is executed.
ACTVT is the activity one can do in that tcode. and DICBERCLS is the authorization group for which the ACTVT is valid.
if you have values ACTVT as 3 (display ) and DICBERCLS is "par" you can see all the tables which are included in authorization group par. and if you have ACTVT as 2 (change) then you can edit the tables in authorization group par.
How to lock or unlock transactions in SAP
There are some transactions that has to be locked in some sittuations, like se01 when system maintenance is going on like se01 or there are some critical transactions like scc5 that has to be locked... To lock such transactions we use sm01. After execution sm01 and selecting a particular transaction by entering in the search field
just check the field along the tcode and the transaction code will be locked. TO unlock the tcode just uncheck the check button
The se16 T-code
This code is used to view table data. This is a high data security risk since the user can access confidential data. It also causes performance hit when large tables are viewed. This tcode must be restricted to few users or firefighter ids.
You can see the initial screen. Here we enter the table name to be viewed and hit the enter button and click on the view data button .
You will see the next selection fields appear as shown below. YOu have to enter your selection criteria so that only selected data can be view. Normally almost all tables are large in size so its better to view only selected data. IF you try to view the whole data of the table it takes long time to display and performance of the server get s hit .
S_TABUS_DIS is checked for authorization of SE16. One can give display activity ( 03) only to and end user for this tcode and authorization group DICERBLS field is also checked. give 03 activity and authorization group which the user belongs to for restricting access.
The user must be in a particular USER group like FI to view FI tables or CO to view CO tables. Without user group assignment one cannot see the respective tables. These user groups are maintained using tcode SUGR. These user groups are different from the logon user groups which has entirely different purpose
How to get the list of users authorized for a Particular TCODE
Goto SUIM then drill down
user --> complex selection criteria --> by transaction authorizations and enter the tcode click on execute button
then you will see a screen as below

How to lock a user in SAP
Goto SU01
enter the userID to be locked in the user field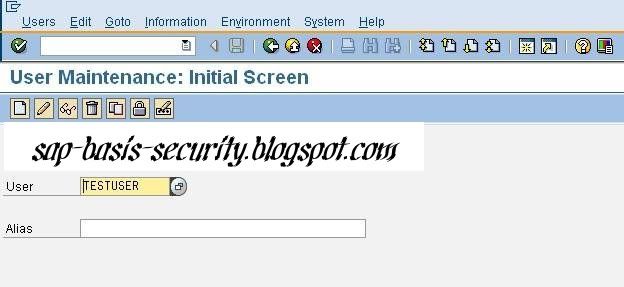
and click on lock button  Then you will see the the following screen if the user is already locked.
Then you will see the the following screen if the user is already locked.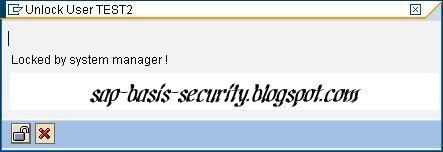
click on the unlock button at the bottom left of the window and the user will be unlocked.
to lock a user again enter the user id in the user field and click on lock button 
and you will see the following screen
now press on the lock button to lock the user...
you can also lock the user at database level. login to the system database..then run a query to update the USR02 table.
To lock an user.
SQL> UPDATE USR02 SET UFLAG = '64' where BNAME='USERID' AND MANDT='CLIENT'
SQL> COMMIT
To unlock an user use
SQL> UPDATE USR02 SET UFLAG = '0' where BNAME='USERID' AND MANDT='CLIENT'
SQL> COMMIT
Here the different values of uflag have different meaning
UFLAG value
- 0 ------ Not locked
- 16 ------ Mystery values
- 32 ------ Locked by CUA admin
- 64 ------ Locked by system Administrator
- 128 ------ Locked due to incorrect logon attempts or too many failed attempts
- 192 ------ A combination of both. The user is locked by admin and user tries to logon with incorrect passwords and gets locked ( 192 = 64+128)
How to list all transactions executable for a role.
Goto SUIM----> transactions----> executable for role.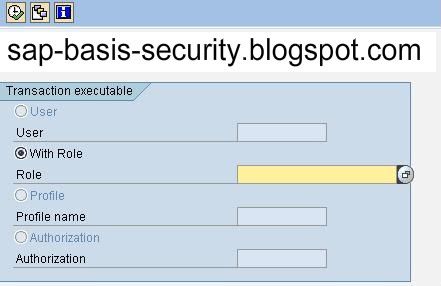
and enter the role name and press F8 to get the results.
but this gives only tcode in the menu of the role.
It will not show the tcodes that are added manually to the role in S_TCODE object.
To find all tcode executable for role along with the tcode that are present in the tcd field..
goto se16 enter agr_1251 and click on data browser button 
enter the role name in agr_name field and enter tcd in FIELD field ash shown in figure.
Then click on execute button  or press F8 to execute and you will see the list of tcodes executable for that role as below
or press F8 to execute and you will see the list of tcodes executable for that role as below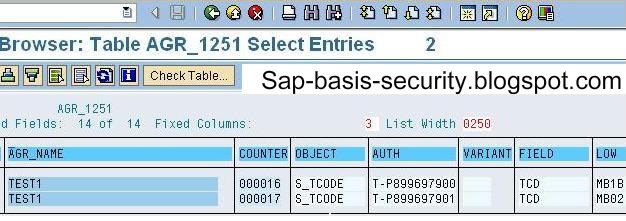
What is a SAP Landscape?
it is a collection of system which are connected throug TMS (transport management system).
The standard and recommend landscape is three system Landscape as shown in figure
Here a new tcode or new program is developed in Development system and is transported to Quality system. Then it is tested on smaple data present in the QA system and then transported to production only if tests are successfull.
The transport flow is
DEVELOPMENT --------> QUALITY -----------> PRODUCTION.
There are no reverse routes.
export(development) ---->import(quality)----> import(production)
nut there are much more complicated landscapes out there..
some contains sandbox systems, some contains demo systems.
Authorization Analysis
- Choose the menu path System -> Utilities -> Display Authorization Check or transaction code SU53. You now can analyze an error in your system that just occurred because of a missing authorization.
- You can call Transaction SU53 in all sessions, not just in the session in which the error occurred. Authorization errors in other users' sessions, however, cannot be analyzed from your own session.
- In the below example, user Bob calls Transaction VA03 (display sales order). The message "You do not have authorization for Transaction VA03" appears. User Bob now chooses transaction code /nSU53 and the system displays the authorization object that was just checked and, for comparison purposes, the values of the object that user Bob has in its user master record. In this case the user Bob don’t have VA03 assigned to any of his role.
- Transaction SU56 allows the user to see what current authorizations are in his buffer

Authorization Trace ST01
You can analyze authorizations as follows: Choose Tools -> Administration -> Monitor -> Traces -> SAP System Trace or Transaction ST01.
Choose trace component Authorization check and pushbutton Trace on. The trace is automatically written to the hard disk.
To limit the trace function to your own sessions, choose Edit -> Filter -> Shared. Enter your user ID in field Trace for user only in the displayed dialog box.
Once the analysis is completed, choose Trace off.
To display the results of the analysis, choose Goto -> Files/Analysis or the pushbutton File listSelect the required file and choose Analyze.
- The results of the authorization check are displayed in the following format: :=
- The return code shows whether or not the authorization code was successful.
- ST01 Return Code
| 0 | Authorization check passed |
| 1 | No Authorization |
| 2 | Too many parameters for authorization check |
| 3 | Object not contained in user buffer |
| 4 | No profile contained in user buffer |
| 6 | Authorization check incorrect |
| 7,8,9 | Invalid user buffer |

Checking your program Background Job Status
Checking your job status with SM50 (processor type BTC) is more accurate then SM37. SAP updates the tables TBTCO wheneveryour background jobs status change. If SAP is shutdown, the currentjobs might not be update ontime to the table. (e.g. a background job wasshown as Active (SM37), in fact it real status should be Cancelled.
The type of work process:
- DIA - work process for executing dialog steps in user transactions
- UPD - update process for executing U1 (time-critical) database changes
- UP2 - update process for executing U2 (non-critical) database changes
- ENQ - for setting and releasing locks on SAP lock objects
- BTC - for executing background jobs
- SPO - for spool formatting processes
How to modify the multiple step program variant?
Go to tcode SM37
- At the Job Overview screen, position your cursor at the scheduled jobs you want to changed (the jobs status must still be Released)
- Click Job -> Change
- Click the Steps button -> here you can move, add or delete addition programs steps to be run


- Double click the program name you want to change
- Click the Print specifications button if you want to change the SAP printers
How To Delete a Scheduled Job in sap
I am working in production support and have been asked to stop a scheduled jobs. The job will run on the first of next month and I need to stop it from running.
To delete a job:
Go to Transaction SM37. Select a job (or jobs) from the Select Background Jobs screen. In the Job Overview, mark the job or jobs you want to delete by checking the box to the left of the job name. Choose Job --> Delete.

Deleting Jobs That Have Dependent Jobs:
If you delete a job that must be processed before another job can be started, the dependent job can no longer be started. The system will inform you of any such existing dependent, or successor, jobs. You'll then need to either reschedule or delete the dependent job.
If you try to release a job whose predecessor job was deleted, the system sets the status of the job to Planned. To start this job, you must release it and specify the start conditions.
What is the use of Authorization Checks?
To ensure that a user has the appropriate authorizations when he or she
performs an action, users are subject to authorization checks.
The following actions are subject to authorization checks that are performed
before the start of a program or table maintenance and which the SAP
applications cannot avoid:
· Starting SAP transactions (authorization object S_TCODE)
· starting reports (authorization object S_PROGRAM)
· Calling RFC function modules (authorization object S_RFC)
· Table maintenance with generic tools (S_TABU_DIS)
In coming posts, we will see how to add authorization checks for Reports and
transactions.
Today we will discuss about table authorization checks.
Purpose of assigning authorization groups for tables:
You can assign authorization groups to tables to avoid users accessing tables
using general access tools (such as transaction SE16). A user requires not only
authorization to execute the tool, but must also have authorization to be permitted
to access tables with the relevant group assignments. For this case, we deliver
tables with predefined assignments to authorization groups. The assignments
are defined in table TDDAT; the checked authorization object is S_TABU_DIS.
Now we will see how to assign/create authorization group for a table:
Go to SE54, Give the table name and choose authorization group and then click
on create/change. You can
create an authorization group.
Example:
You can assign a table to authorization group Z001. (Use transaction SM30 for
table TDDAT) A user that
wants to access this table must have authorization object S_TABU_DIS in his or
her profile with the value
Z001 in the field DICBERCLS (authorization group for ABAP Dictionary objects).
Authorization Check:
In the earlier post, we came to know the importance of authorization check in real
time environment. We know how to check authorization for table maintenance.
(Please refer earlier post).
Now we will see how to check authorization for Reports, Transactions, RFC
function modules.
The following actions are subject to authorization checks that are performed
before the start of a program or table maintenance and which the SAP
applications cannot avoid:
Starting SAP transactions (authorization object S_TCODE)
starting reports (authorization object S_PROGRAM)
Calling RFC function modules (authorization object S_RFC)
Table maintenance with generic tools (S_TABU_DIS)
The authorization objects S_TCODE, S_PROGRAM, S_RFC, and S_TABU_DIS
are standard SAP provided.
Creating a new authorization object is not in the scope of ABAP developer. It will
be taken care by SAP BASIS team.
To add authorization check to your program, you need to add the following code in
your report. Imagine that you have created a transaction code for your report, then
you should use the authorization object S_TCODE to check the authorization.
You can place the code in initialization event.
*Initialization
INITIALIZATION.
AUTHORITY-CHECK OBJECT 'S_TCODE'
ID 'TCD' FIELD 'ZEXAMPLE'.
IF sy-subrc <> 0. "Not Authorized
MESSAGE e003(ZZ) WITH 'TCD' 'ZEXAMPLE'.
ENDIF.
Here zexample is the transaction code created for the report.
SAP Authorization Concept
The SAP authorization concept is based upon the logical relationship between a user ID and the range of system authorizations with which it can be associated. The architecture of the authorization system is based upon the utilization of several individuals but related logical components: Profiles, Objects, Fields, and Authorizations. The user ID refers exclusively to profiles. Each profile grants a set of specific system access authorizations to user.
Composite profiles refer to the various employee roles available in the corporation (for instance: Purchasing / Receiving Clerk or Accounts Agent). As the name suggests, composite profiles may contain multiple user IDs necessary to perform all the business operations associated with a particular role. A composite profile may encapsulate another composite profile(s). In practice, a model composite profile should be recognized for each possible role in the organization, which may be used to produce hybrid composite profiles. The over-existence of the hybrids can defy the very purpose of composite profiles and they should be created only when specific needs arise.
User Ids
User ids allow access to SAP applications. Each user must have a corresponding profile specifically assigned. In many situations, multiple composite profiles can be assigned to a user ID, depending on the role(s) an individual user is responsible for, in the business processes.
Authorizations
An authorization process may ask for second associated authorization process which in turn asks for third and so on. For example, the task of paying a vendor invoice may require 10 different authorizations.
Authorization Check
The following actions are subject to authorization checks that are performed
before the start of a program or table maintenance and which the SAP
applications cannot avoid:
Starting SAP transactions (authorization object S_TCODE)
starting reports (authorization object S_PROGRAM)
Calling RFC function modules (authorization object S_RFC)
Table maintenance with generic tools (S_TABU_DIS)
The authorization objects S_TCODE, S_PROGRAM, S_RFC, and S_TABU_DIS
are standard SAP provided.
Creating a new authorization object is not in the scope of ABAP developer. It will
be taken care by SAP BASIS team.
Listing TCODE transactions used to view what users are logged in to SAP
I want to get a list of all transactions used per user in a specific time period. Basically I’m looking for a list of all users logged in SAP and the details of the tcodes they used. Is there any standard report or tcode available to view this info?
There is no standard transaction. The information is available for configurable time periods using transaction ST05N but it is not organized to readily provide a report of users and transactions. Also the information available summarizes a user’s use of a transaction. There will be one entry (with count data) per user per time period. Daily, weekly and monthly summaries can be created and they are stored for configurable durations.
The information is summarized into a cluster table called MONI based on the STAT files that are written in the file system and regularly refreshed. MONI cannot be queried via SE16 etc., but SAP delivers a number of function modules that retrieve data from these tables.
It is also possible to configure audit logging via SM19 and read the log files via SM20. This will provide more detail but it also introduces new file management issues and requires a change to system settings.
SAP’s TCODE checks with the authorization tool
What are the checks that the SAP authorization tool performs when a TCODE is executed in order to ensure authorization of that user?
When initiating a transaction, a system program performs a series of checks to ensure the user is authorized.
1. The program checks whether the transaction code exists in table TSTC.
2. The program checks whether the transaction code is locked by the administrator (transaction code SM01).
3. The program checks whether the user has the authority to start the transaction. Authorization object S_TCODE (transaction start) contains the authorization field TCD (transaction code). The user must have the appropriate authorization for the transaction code to be started (for example, FK01, Create Vendor).
4. The program checks whether an authorization object is assigned to the transaction code. If this is the case, the program checks whether the user has an authorization for this authorization object. The transaction code/authorization object assignment is stored in table TSTCA.
Note: An SAP program controls steps 1 through 4. It displays an automatic message to the user if an authorization attempt fails in the step.
5. The system performs authorization checks in the ABAP program using the ABAP statement AUTHORITY-CHECK.
What are the Authorizations Required
Administrators who use the Profile Generator require authorization for the following authorization objects: S_USER_AGR Authorization Check for Activity Groups
S_USER_TCD Transaction Assignment of Transactions to Activity Groups
S_USER_GRP User Master Maintenance: User groups
S_USER_PRO User Master Maintenance: Authorization Profile
S_USER_AUT User Master Maintenance: Authorizations
S_USER_VAL Maintenance of Authorization Values in Activity Groups
topics
-
▼
2008
(397)
-
▼
May
(85)
- SAP Business One Citrix Installation Guide free do...
- Installation Guide for MiniSAP 4.6D Steps free dow...
- MCOD tech Installation Steps free downloads
- SAP 4.7 Installation on UNIX Steps free downloads
- SAP GUI 710 Installation Guide free downloads
- Multinational SAP Implementation Steps free downloads
- CRM Installation Guide free downloads
- EP Installation Guide With Screenshots free downloads
- XI Installation Guide With ScreenShots free downloads
- SAP WEB AS Installation On Windows Oracle steps
- SAP Netweaver JDI steps free downloads
- GUI Installation for Mass Users Steps free downloads
- Oracle Installation Steps free downloads
- Installation of SAP WEBAS ABAP J2EE Steps
- Post and Pre Installtion procedure
- Solution manager 4.0 on Windows Oracle Steps free ...
- Installation of SAP R3 4.7 Steps free downloads
- GUI Installation Steps free downloads
- Solution Manager 7.0 Installation Steps free downl...
- BIW 3.5 Installation Steps free downloads
- ECC 5.0 Installtion Steps free downloads
- ECC 6.0 Installation screen shots free downloads
- solution manager Material free downloads
- Profiles
- Sarbanes - Oxley(SOX) Material free downloads
- AIS Implementation Material free downloads
- Generating profiles using Automatic Profile Genera...
- Security Audit Log Material free downloads
- SAP Security Guide Volume 1 & 2 Material free down...
- Operation modes Overview Material free downloads
- AIS - audit management preparation.sim Material fr...
- Profile Parameters Material free downloads
- SAP Security HandBook free downloads
- Implementing OSS notes using SNOTE Material free d...
- Saint SAP Add On Installation Materail free downloads
- Applying Hot Packages Using OSS Material free down...
- spool administration snap shots Free downloads
- Homo-Hetro System Copy For WEB AS 620 Material fre...
- System copy procedure & DB refresh Free downloads
- Transports.ppt Material free downloads
- Creating Change Request And Change Task
- TMS Configuration Material free dwonloads
- STMS Material free downloads
- JAVA Troubleshooting Guide For WEB AS Installation
- Troubleshooting XI,Debug XI3.0 material free downl...
- general problems in sap r/3 material free downloads
- Creating Multiple R3 Users using SCATT free downloads
- SCOT Configuration Material free download
- SAP Upgrade Guide Material free downloads
- SAP Performance Tuning material free download
- Split Mirror Disk Backup For Oracle Material free ...
- Database Security For Oracle material free downloads
- Oracle Upgrade Master Guide 9i To 9.20 free downloads
- Migrating Or Upgrading To Oracle Ver : 8.0.5 free ...
- Client adminstration Material free download
- How to Use CCMS free downloads
- BR Tools Screen Shots free download
- Remote Services- OSS- SAP Net- Early Watch
- SAP Router700 free download
- Using Tivoli to manage Large Scale R3 Environment
- SAP System Measurement Guide free download
- SAP R3 Administration Press Book free download
- SAP System Administration Made Easy- MS SQL free d...
- Basis Weeks Material free download
- System Administration Tasks,SPAM,KERNEL,CLIENT COP...
- SAP R3 Handboook Edition -3 Free download
- T-code sa38
- T-code SU24
- What is and authorization object
- How to lock or unlock transactions in SAP
- The se16 T-code
- How to get the list of users authorized for a Part...
- How to lock a user in SAP
- How to list all transactions executable for a role.
- What is a SAP Landscape?
- Authorization Analysis
- Checking your program Background Job Status
- How to modify the multiple step program variant?
- How To Delete a Scheduled Job in sap
- What is the use of Authorization Checks?
- SAP Authorization Concept
- Authorization Check
- Listing TCODE transactions used to view what users...
- SAP’s TCODE checks with the authorization tool
- What are the Authorizations Required
-
▼
May
(85)


